Love.Law.Robots. is moving!
You're browsing the original version of the Love.Law.Robots. Check out the new site. It's prettier and packs loads of new features!
Detox your accounts with better passwords now!
 `
`
The Problem that no one wants to talk about#

Disgusting practices everywhere…
One of the most intriguing changes in my time online regards passwords. Back in the yahoo and hotmail days, passwords are an annoyance, and you would use the easiest thing — birth dates, ID numbers, mother’s maiden name — to get rid of it. We then had to adjust our strategies when password policies became fashionable. Need a certain length of characters? Need a capital letter, a symbol or a number somewhere? Just l33tspeak something and get rid of that annoying prompt. Multiple accounts? Same password then. Convenience! Life goes on.
Then brute force dictionary attacks became more powerful and data breaches became common. This meant that by the time a hacker figured out what one of your passwords is, they can have all the keys to your online kingdom. It’s no wonder that 80% of hacking related data breaches concern passwords. Heck even the Singhealth incident concerned passwords.
Curious whether you are at risk of being hacked? Check out the have I been pwned website. Now Google is doing its part too. If you use Chrome a lot, I suggest you to take a look and see what Google thinks of your password practices. I did, and I was shocked to see how many compromised, weak and repeated passwords I was using.
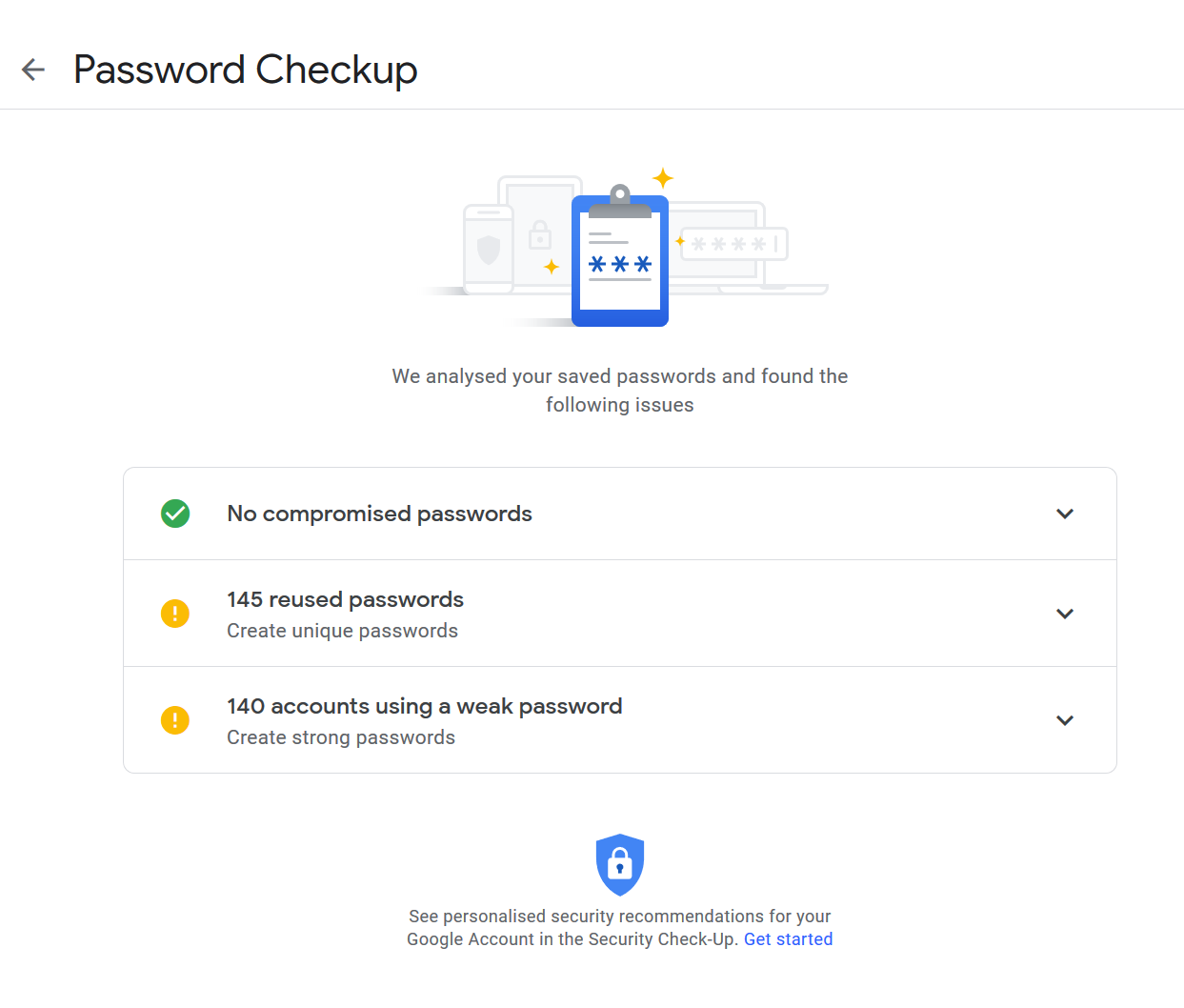
Not feeling so good now right…
Time for Action!#
The prevailing wisdom (at least for now) is to have a long password made up of several words. This fights brute force attacks while still being possible to remember. However, trying to remember several several words for each of our several social media and work accounts is nigh impossible.
Luckily, password managers have become more mainstream. Password managers are programs that helps you to remember a password and makes them available when you need to. Many of them work by having you remember a master password. So you can still have your several word passwords, and remember only one to protect the rest. Examples include LastPass, 1Password and Bitwarden. If you peek into your browser settings (like Google and Firefox), you will find some sort of password manager there.
This of course isn’t fool-proof. Security incidents do happen to password managers. Some people may feel uncomfortable with relying on Google (or even Firefox) as a safe house for all their secrets. Even so, everyone is still better off with a password manager. Even if you feel you are not up to challenge of running your own password manager server (coming next), you should still take the trouble to get one.
Why Passbolt?#

After researching my options, I decided to go with a self-hosted passbolt server. Passbolt is an “open source password manager for teams”. “Self-hosted” means I own the server which will run it and by right the passbolt developers are not in charge or have access to it.
Some of the reasons why I specially chose passbolt are:
- Open Source: I always prefer the open source solution. Besides being “free” (in both senses of the word), the code is open for inspection and is used by several users. Security in transparency; security in its openness.
- Self-hosted: This one is special. As mentioned, security incidents can happen to the best of companies. It might be counter-intuitive at first, but if I ran my own little secrets with my own secrets in my tiny corner of the internet, it is far less likely to be targeted by a professional hacker.
- Teams: When you read “Teams”, it means devops or some system IT thing. However, for me, I do share passwords with my family, so this is a secure and convenient way to do this.
- Free. Enough said. Other options have free tiers, but this one lets me have the whole farm.
That said, passbolt isn’t for everyone. It’s in active development, but missing features include a mobile app and support for Edge and Safari. This excludes a big part of our online lives. Furthermore, running a server is its own challenge. However, if you always wanted to run your own server, passbolt is one of the easiest server applications I had to manage.
If you do not feel up to the task, you can use a more user friendly manager. As the rest of this section talks about passbolt, you can skip to the next section.
Step 1: Spin up your passbolt server#
In the wonderful world of cloud services, you can easily get a cloud server for as little as $5. Passbolt isn’t demanding, so your server can (and mine does) use the cheapest tier.
If you would like a cloud server, I am always partial to DigitalOcean in this regard. _You can use my_** personal referral link**** _on DigitalOcean and get $50 of credits over 30 days._** That is enough credits to play around with passbolt and decide if this is for you.
Once you have your DigitalOcean account, create a $5 Droplet (it’s the cheapest one). There are several ways to install a server, but the most simple one is to use the marketplace to select passbolt and click on Create Passbolt CE Droplet. This automates preparing the server, and you just have to sit back and let the containers do their work.
While you are waiting for your server to start, it’s a good time to prepare your own domain name. This isn’t just an easy way to remember your server, but also to enable SSL. SSL is important for encrypting your communication between you and your server.
If you don’t have one You can pick a domain name from Dynadot. As your domain name is private, you don’t have to use a special one. Pick the cheapest, pick the easiest. I picked an .xyz domain with me and my wife’s nicknames (which I can’t share online :P) The cheapest domains can be obtained for about $1 in the first year, so that’s your only financial overlay so far.
Once you got your domain name, you have to point it to your new droplet. If you are going to use DigitalOcean a lot, having Digital Ocean manage your DNS can be very convenient. You can do this by pointing your domain’s name servers to DigitalOcean’s, then use their nifty dashboards to do your work.
Step 2: Install your passbolt server#
Before you inspect your shiny new passbolt website, you have to obtain some information from the server to finish your install. These are the same instructions as the marketplace page.
Log In to SSH: SS-What?!! If you are going to run your own server, knowing how to SSH will be useful. For now though, you can still probably get by with DigitalOcean’s web browser console.

Locate DigitalOcean’s Console Access for your Droplet.
Follow the instructions (with your new DNS) to set up SSL and the database.
Once the guided setup in the console is done, you have to get the database details of your passbolt server. Type cat /root/.mysql_credentials in the console and you would get an output that looks a bit like this.
username = root
password = [root_password]
username = passbolt_usr_vAAA34b8
password = [user_password]
database = passbolt_YmM8wkgh
Copy these details because you will need it when you go to the web server of passbolt.
Now you are ready to go to your shiny new passbolt web page. Type the domain name you pointed to your passbolt server. If all is working well, GPG and SSL will be shown working. Follow the straightforward instructions to finish the install and set up your first user. This is where your master password will come in, so make it count!
You will also receive your private key. Store this in a good place as you will need it the first time you use passbolt in your web browser.
To send email from your server, you have a few options. I used Gmail. You might find outdated instructions since Google tightened security recently. If you are using your 2FA protected Google account, you will need an App Password. Follow the instructions here (take note especially of step 4 and translate the settings to the form for passbolt) and you can get your emails sent.
Step 3: Install plugins/browser extensions and get to work!#
There are currently two main ways to use your passbolt install — through the web page or browser extensions. I use the browser extension for my day to day surfing while I found the web page useful for non-website stuff like personal access tokens.
The most straightforward way to use it is to use your browser and go to your passbolt web page. It will ask you to download a plugin, download it and use your private key to go to your website. Using the extension button in your action bar, you now have a convenient place to enter and store new passwords. To retrieve your password, you use the plugin to fill the form or click on individual forms to cut and paste passwords wherever you need them.
Since you are going to do a lot of password updating in the next step, it’s a great idea to ask passbolt to Remember until I log out so you do not have to keep entering your master password. Practicing your password is great but you do not want to pass out or get finger cramps.
Time to Detox your Passwords#

Photo by Dan Meyers on Unsplash
After working hard to get your password manager up and running, it’s time to fix this password problem.
It’s easy when you sign up for new accounts — all you have to do is to use your fancy new password manager and ask it to generate a new password.
For your older accounts, unfortunately there is very little you can do except to reset your passwords by visiting each website.
You will need to figure out where they are. Using your web browser’s password library is a great start. I like Google’s password checkup too because it also checks passwords on your Android Apps, which is probably going to be the next source of vulnerability.
If you were like me and balked at the number of passwords , I decided to divide and conquer using the following plan.
- If Google’s Password Checkup says it’s a compromised password, I would try to change that first. Since it is already a liability, it should go first.
- I then try to change passwords for websites I use often. I figured that I am already visiting these sites, so it will be convenient to just change them while I am there. This was my banking accounts, developer accounts and other news websites.
- I did not include Google, Facebook and other passwords which I use on my phone in Step 2. These passwords have a high impact, but are very likely to break things like SSO sign ins, so I would like to take this a bit slower. This might also probably be due to passbolt not having mobile app support currently.
- After steps 1-3, what I am left with are websites with weak, repeated passwords which I do not use often. It’s not true that these sites are of limited threat, but given that I don’t use them often, I probably don’t have critical or updated information on them.
I call this Risk Assessment. It’s trying to deal with a problem by looking at the threat it present, and prioritizing it accordingly. Marie Kondoing your digital life takes a lot of effort and time, and we have better things to do with our lives. Hopefully this gives us a framework to deal with password vulnerabilities.
Do you agree with how I have dealt with the password problem? Did you have success in clearing out your rubbish accounts? I would like to hear you!